The Value of Knowing Your School's Security Weaknesses
Many schools in California are rolling out "one-to-one" computing initiatives, to supplement existing policies of bring your own device (BYOD) programs to advance digital curriculum in K-12.
These changes provide amazing educational opportunities for students and staff alike, but introduce new challenges. One of the most pressing is ensuring security while more than doubling the endpoints involved.
We believe that intelligence and visibility are powerful, particularly when it comes to cyber-security threats and the defense against them. K-12 schools are particularly vulnerable targets because they have transient and often novice populations. Today's students are digital natives who are very savvy with networks and devices; in many cases more than school administrators or even IT staff.
Unfortunately, security of local infrastructure is not a concern for most students, and K-12 environments have earned a reputation as "soft targets." Ransomware criminals are able to take advantage of simple weaknesses in policies, software, or network architecture.
Research consultant Doug Levin of EdTech Strategies put together a K-12 Cyber-Incident Map, which graphically illustrates the impact of cyber incidents around the country.
As K-12 schools increase their reliance on digital devices, the number of cyber incidents has grown exponentially. Between Jan 01, 2016 through the end of 2017, there has been a 100% increase in publicly disclosed cyber incidents, no doubt a fraction of all incidents taking place. (Source: THEJournal.com)
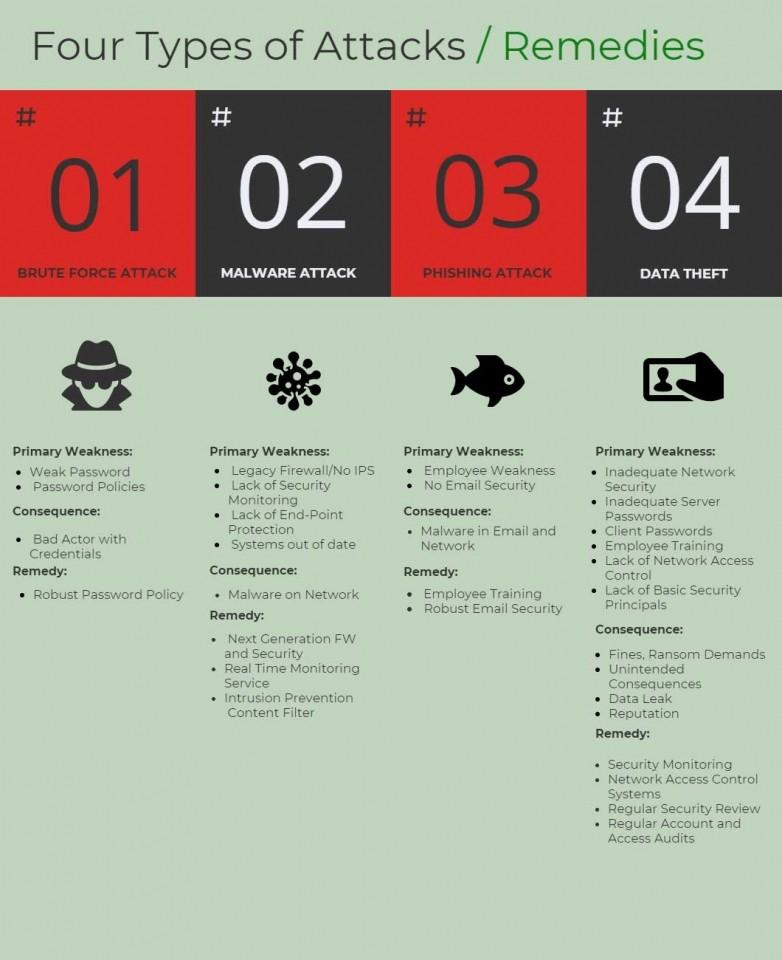
The following areas represent some common fields of attack by cyber-criminals. Cyber-attacks come in many different forms in K-12 environments. No single security product will keep a K-12 campus safe; a "defense in depth" security approach is required to ensure the greatest protection.
Any successful approach to security should incorporate a detailed review and assessment of one's present and ongoing security posture. Security solutions, both hardware and software, can be expensive and drain scarce resources from other key areas like wireless infrastructure or digital textbooks. The most important first step is to understand where the largest risks are to potential data-theft or cyber-attacks.
Read the full article on Datalink Networks' Technology Blog.

Comments